Access la tatangital
It means gaining entry into a computer, computer system or computer network. [Section 2(1)(a)].
Addressee
It means a person who is intended by the originator to receive the electronic record or the information sent via a computer system. However, the definition does not include any intermediary. [Section 2(1)(b)].
Affixing Electronic Signature
‘Affixing electronic signature’ means authentication of an electronic record by means of digital signature. [Section 2(1)(d)] This indicates his authority as well as the authenticity of the document.
Asymmetric Crypto System
‘Asymmetric Crypto System’, according to the definition of Section 2(1)(f) of the Information Technology Act, 2000, means a key pair that provides safety and authenticity to the electronic records being transmitted.
The key pair consists of a public and a private key, both of which are needed to ‘sign’ an electronic document digitally.
Communication Device
The definition includes cell phones, personal digital assistance devices or a combination of both or any other device used to communicate, send or transmit text, video, audio information or even an image. [Section 2(1) (ha)]
Learn and Read More CS Executive JIGL Question and Answers
Computer
The definition includes any electronic, magnetic, optical or other high-speed data processing device or system that performs logical, arithmetic, and memory functions, by way of manipulations of electronic, magnetic or optical Data.
It includes all input, output, processing, storage, computer software, or communication facilities which are connected or related to the computer in a computer system or computer network. [Section 2(1)(i)]
Computer Resource
It means and includes a computer, computer system, computer network, data, computer database or software. [Section 2(1)(k)]
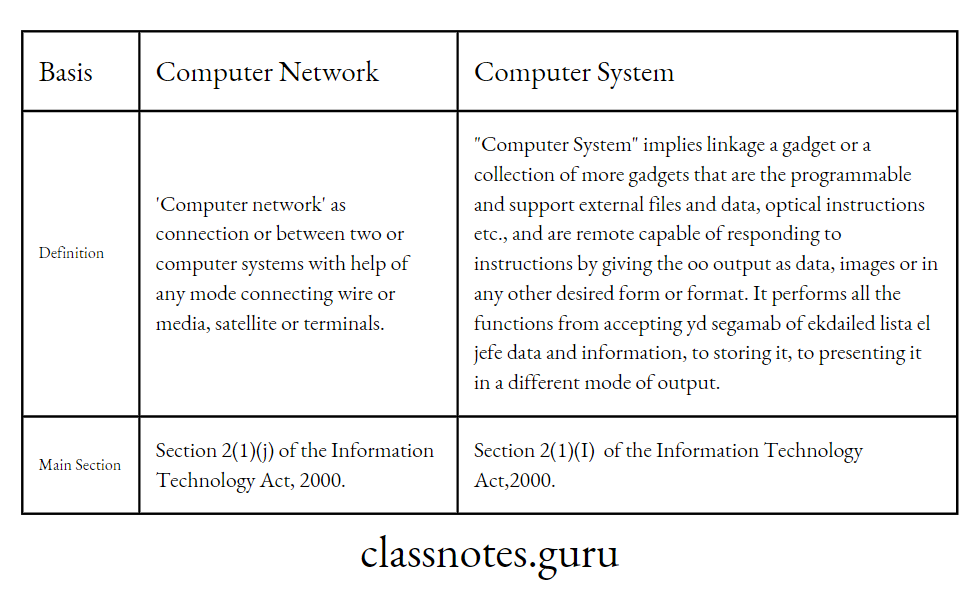
Computer System
It means a device or collection of devices, including input and output support devices and excluding calculators which are not programmable and capable of being used in conjunction with external files, which contain computer programmes, electronic instructions, input data, and output data, that performs logic, arithmetic, data storage and retrieval, communication control and other functions. [Section 2(1)(I)]
Communication Device
It includes all devices used to convey or communicate any text, video, audio or image, like cell phones or other digital communication devices. [Section 2(1) (ha)].
Computer Network
It is the interconnection of one or more computers through satellite, microwave, terrestrial line or other communication media; and includes terminals or a complex consisting of two or more interconnected computers.
The definition includes all these elements even if the interconnection is not continuously maintained. [Section 2(1)(j)]
Cyber Cafe
It means any facility that offers access to internet to the public, in the ordinary course of business. [Section 2(1)(na)].
Cyber Security
It implies protecting information, equipment, devices, computer, computer resource, communication device and information stored therein from unauthorised access, use, disclosure, disruption, modification or destruction. [Section 2(1)(nb)].
It ensures the authenticity and safety of information, so that it can be relied upon by users.
Digital Signature
‘Digital Signature’ is defined in Section 2(1)(p). This definition provides for Electronic means of validating of electronic records by the procedure prescribed under the Information Technology Act, 2000.
Domain Name
‘Domain Name’ is a unique address pertaining to a website. This is where all communications using the net will be addressed. It helps to register the domain name as the address then becomes exclusive and identifies the company or person whose website it is. It also makes finding the company online easier.
Offences and penalties under the Act
‘Electronic Record’ as per Section 2(1)(t) includes information recorded by way of data or images in electronic form and recorded in any media, viz,microfilm, microfiche etc.
Electronic Signature
It is a means of authenticating electronic records by a subscriber by means of affixing digital signature. It is as per the Second Schedule to the Act. [Section 2(1)(ta)]
Electronic Signature Certificate
It means an Electronic Signature Certificate issued under Section 35. It is inclusive of a Digital Signature Certificate. [Section 2(1)(tb)].
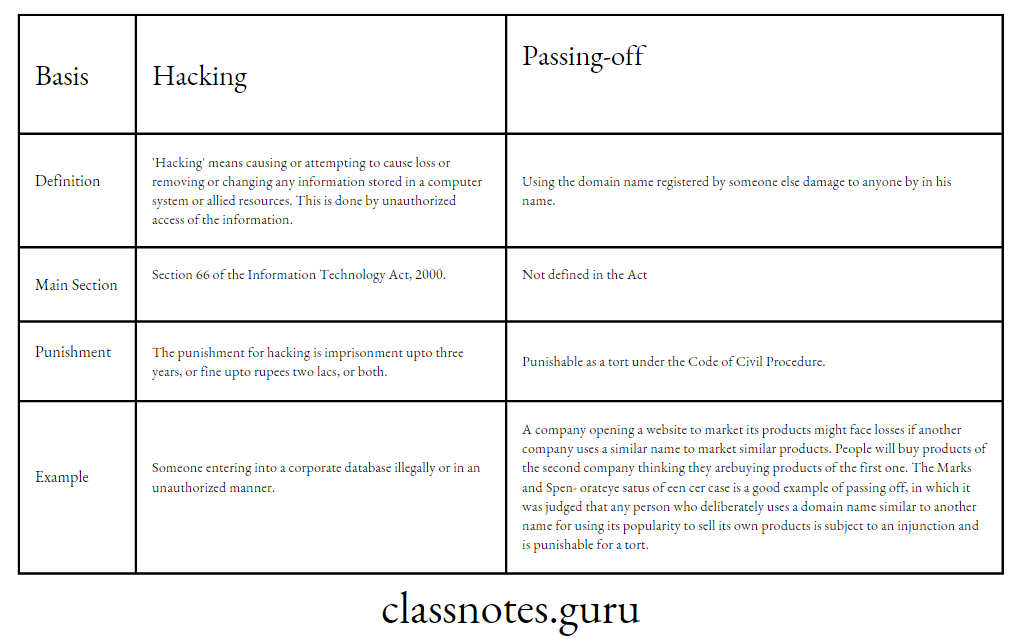
Hacking
‘Hacking’ means causing or attempting to cause loss or damage to anyone by removing or changing any information stored in a computer system or allied resources. This is done by unauthorized access of the information.
The punishment for hacking is imprisonment upto three years, or fine upto rupees two lacs, or both. (Section 66)
Information
It includes data, message, text, images, sound, voice, codes, computer programmes, software and data bases or micro film or computer generated micro fiche. [Section 2(1)(v)].
Intermediary
Intermediary in context of electronic records means any person who receives, stores or transmits that record on behalf of another person or provides any service with respect to that record.
The definition includes telecom service providers, network service providers, internet service providers, web hosting service providers, search engines, online payment sites, online-auction sites, online-market places and cyber cafes; [Section 2(1)(w)]
Key Pair
The Key Pair consists of a public and a private key, both of which are needed to ‘sign’ an electronic document digitally. [Section 2(1)(x)]
Network Service Providers
‘Network Service Providers’ have been defined in Section 2(1)(w) of the Information Technology Act, 2000. These are intermediaries who do not initiate the creation or passing off a message but help in providing facilities for the same.
Originator
‘Originator’ means a person who sends or initiates an electronic message. This excludes all intermediaries who just act as a link between the sender and recipient of messages. [Section 2(1)(za)]
This definition helps to judge the authenticity of messages, i.e. if a message has been sent by a known originator, then it can be deemed to be authentic.
Passing off
‘Passing off’, although not defined in the Act, means using the domain name registered by someone else in his name. This is punishable as a tort, as it might result in financial and other losses to the person who is the original owner of the domain name.
For example, a company opening a website to market its products might face losses if another company uses a similar name to market similar products.
Private Key
It is the key of a key pair that is used to create a digital signature. [Section 2(1)(zc)]
Public key
It is the key of a key pair, used to verify a digital signature and listed in the Digital Signature Certificate. [Section 2(1)(zd)] acheall to
Secure system
‘Secure system’ means computer hardware, software, and procedures that-
- are reasonably secure from unauthorised access and misuse;
- provide a reasonable level of reliability and correct operation;
- are reasonably suited to performing the intended functions; and
- adhere to generally accepted security procedures; It is deemed to be secure when it is as per the requirements of Section 15 of the Information Technology Act, 2000.
They are as under – If the signature is unique and controlled by the person affixing it.
It distinguishes the subscriber, i.e. the person affixing or using it. It is so linked with the electronic record to which it is attached that if the record were changed in any way, doing so would nullify the authenticity or veracity of the signature.
Verify
To verify a digital signature or electronic record means to determine whether –
- the initial electronic record was affixed with the proper digital signature by the use of the right and authorized private and public key combination of the subscriber; and that
- the initial electronic record is retained intact, or
- if it has been altered since, such electronic record was so affixed with the proper digital signature. [Section 2(1)(zh)].
Descriptive Questions
Question 1: Explain the provisions for renewal of licence of Certifying Authority as per Information Technology Act, 2000.
Answer:
Renewal of license:
A Certifying Authority can apply for renewal of license not less than forty-five days before the date of expiry of the period of validity of licence and comply all the rules of Information Technology (Certifying Authorities) Rules, 2000 which are applied in case of fresh application for becoming certifying Authority.
The Controller may, on receipt of an application for appointment as certifying authority, after considering the documents accompanying the application and such other factors, as he deems fit, grant the licence or reject the application.
No application for becoming certifying Authority shall be rejected under unless the applicant has been given a reasonable opportunity of presenting his case.
Question 2: Comment on the punishment for publishing or transmitting obscene material in electronic form as stated in section 67 of Information Technology Act, 2000.
Answer:
Punishment for Publishing or Transmitting of material obscene material in electronic form:
As per Section 67 of the Information Technology Act, 2000 whoever publishes or transmits or causes to be published or transmitted in the electronic form, any material which is lascivious or appeals to the prurient interest or if its effect is such as to tend to deprave and corrupt persons who are likely, having regard to all relevant circumstances, to read, see or hear the matter contained or embodied in it, shall be punished on first conviction with imprisonment of either description for a term which may extend to three years and with fine which may extend to five lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to five years and also with fine which may extend to ten lakh rupees.
Question 3: Discuss ‘Digital Signature’ and ‘Electronic Signature’ under the Information Technology Act, 2000.
Answer:
‘Digital Signature’ and ‘Electronic Signature’ under the Information Technology Act, 2000
‘Digital signature’ is defined in Section 2(1)(p). This definition provides for electronic means of validating of electronic records by the procedure prescribed under the Information Technology Act, 2000.
This is done with the help of a signature in electronic form, which is registered with the Certifying Authority under the Act. Affixing electronic signature ‘Affixing electronic signature’ means authentication of an electronic record by means of digital signature [Section 2(1)(d)].
This indicates the signatory’s authority as well as the authenticity of the document. Section 3A of the Act provides for authentication of electronic records with the aid of digital signature or other electronic authentication technique.
Question 4: Discuss the liability of Corporate body for data protection under Information Technology Act, 2000.
Answer:
The liability of Corporate body for data protection under Information Technology Act, 2000
Section 43A of the Information Technology Act, 2000 lays responsibility of maintaining the security of sensitive personal data or information contained in its computers resources.
If, because of insufficient security, there is some loss of such data, or a wrongful gain to a party from such data, the corporate body shall be liable to pay compensation by way of damages to the person who suffers a loss because of such negligence to maintain security.
Security here implies maintaining data integrity as well as restraining unauthorized access to such data. Usually, there is a clause to this effect in the contract signed between the party giving such information and the corporate body receiving it.
Question 5: If any person dishonestly or fraudulently does any act under section 43 of Information Technology Act, 2000 without the permission of the owner or any other person, who is incharge of a computer, computer system network, he shall be punished. What is the punishment for this offence? In brief, discuss the offences listed in The IT Act relating to computer and computer system network.
Answer:
If any person, dishonestly or fraudulently, does any act referred to in Section 43 of the Information Technology Act, 2000, he shall be punishable with imprisonment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both. (Section 66 of the Information Technology Act, 2000)
The offences listed in the Information Technology Act, 2000 are as follows:
- Dishonestly receiving stolen computer resource or communication device
- Identity theft
- Cheating by personation by using computer resource
- Violation of privacy
- Cyber terrorism
- Publishing or transmitting of material containing sexually explicit act, etc., in electronic form
- Publishing or transmitting of material depicting children in sexually explicit act, etc., in electronic form
- Misrepresentation
- Breach of confidentiality and privacy
- Disclosure of information in breach of lawful contract
- Publishing electronic signature Certificate false in certain particulars
- Publication for fraudulent purpose.
Question 6: Describe the documents or transactions to which the Information Technology Act, 2000 shall not apply. (4 marks)
Answer:
Following documents or transactions to which the Information Technology Act, 2002 shall not apply:
- A negotiable instrument (other than a Cheque) as defined in section 13 of the Negotiable Instruments Act, 1881.
- A power-of-attorney as defined in section 1A of the Powers-of-Attorney Act, 1882.
- A trust as defined in section 3 of the Indian Trust Act, 1882.
- A will as defined in clause (h) of section 2 of the Indian Succession Act, 1925, including any other testamentary disposition by whatever name called.
- Any contract for the sale or conveyance of immovable property or any interest in such property.
Question 7:Discuss the provisions of Sections 14 and 15 of Information Technology Act, 2000, on secure electronic records.
Answer:
Secure Electronic Records:
‘Asymmetric Crypto System’, according to the definition of Section 2(1)(f) of the Information Technology Act, 2000, means a key pair that provides safety and authenticity to the electronic records being transmitted.
The key pair consists of a public and a private key, both of which are needed to ‘sign’ an electronic document digitally.
Secure System:
‘Secure system’ means computer hardware, software, and procedures that-
- are reasonably secure from unauthorised access and misuse.
- provide a reasonable level of reliability and correct operation.
- are reasonably suited to performing the intended functions; and
- adhere to generally accepted security procedures.
When the security procedure has been applied to an electronic record at a specific point of time, then such record is deemed to be a secure electronic record, from such point of time to the time of verification. (Section 14) It is deemed to be secure when it is as per the requirements of Section 15 of the Information Technology Act, 2000. They are as under –
- If the signature is unique and controlled by the person affixing it.
- It distinguishes the subscriber, i.e. the person affixing or using it.
- It is so linked with the electronic record to which it is attached that if the record were changed in any way, doing so would nullify the authenticity or veracity of the signature.
Question 8 : Explain the procedure for obtaining ‘Electronic Signature Certificate’ under the Information Technology Act, 2000.
Answer:
Procedure for obtaining an Electronic Signature Certificate it means an Electronic Signature Certificate issued under Section 35. It is inclusive of a Digital Signature Certificate. [Section 2(1) (tb)].
These are dealt with in Section 35-39 of the Act. Section 35 of the Act authorises the Certifying authority to issue electronic signature certificates.
Application-Whoever requies a DSC or electronic signature may apply in the prescribed form, along with the requisite fees, to the Certifying Authority. The form and fees for such is prescribed by the Central Government.
The application shall also have attached to it a certification practice statement or a statement containing such particulars as are specified by regulations.
On the receipt of such an application and after due enquiries, the Certifying Authority may grant or reject the electronic signature Certificate. In the case of the latter, the reasons have to be recorded in writing.
However, no application shall be summarily rejected, without adequate reasons for the same.
Question 9: Elaborate the offences relating to computers and connected matters therein.
Answer:
Offences related to computers and related matters:
The Information Technology Act, 2000 provides for penalties adjudicated before adjudication officers, as per Sections 43-47, for offences related to computers and related matters.
Section 43 also talks of “penalty and compensation for damage to computer, computer system”. Section 43 of the Act provides for penalty for damages inflicted on a computer or computer resource, without the owner’s permission or knowledge.
The damages are to be paid by way of compensation upto an amount of rupees one crore.
The offences it covers are as follows:
If anyone:
- accesses or secures access to such computer, computer system or computer network or computer resource;
- downloads, copies or extracts any data, computer data base or information from such computer, computer system or computer network including information or data held or stored in any removable storage medium;
- introduces or causes to be introduced any computer contaminant or computer virus into any computer, computer system or computer network;
- damages or causes to be damaged any computer, computer system or computer network, data, computer data base or any other programmes residing in such computer, computer system or computer network;
- disrupts or causes disruption of any computer, computer system or computer network; (f) denies or causes the denial of access to any person authorised to access any computer, computer system or computer network by any means;
- provides any assistance to any person to facilitate access to a computer, computer system or computer network in contravention of the provisions of this Act, rules or regulations made thereunder;
- charges the services availed of by a person to the account of another person by tampering with or manipulating any computer, computer system, or computer network;
- destroys, deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means;
- steal, conceal, destroys or alters or causes any person to steal, conceal, destroy or alter any computer source code used for a computer resource with an intention to cause damage; he shall be liable to pay damages by way of compensation to the person so affected.”
As per Section 65 in The Information Technology Act, 2000, “whoever knowingly or intentionally conceals, destroys or alters or intentionally or knowingly causes another to conceal, destroy, or alter any computer source code used for a computer, computer programme, computer system or computer network, when the computer source code is required to be kept or maintained by law for the time being in force, shall be punishable with imprisonment up to three years, or with fine which may extend up to two lakh rupees, or with both.”
Question 10: What is the liability of network service provider for contravention of Information Technology Act, 2000?
Answer:
The liability of network service provider for contravention of Information Technology Act, 2000
‘Network service providers’ have been defined in Section 2(1)(w) of the Information Technology Act, 2000. These are intermediaries who do not initiate the creation or passing off a message but he’p in providing facilities for the same.
They can help in the receiving or sending of a message on behalf of another.
Section 79 of the Act exempts them from liability they might incur for the actions of third parties making use of their services and doing something that is expressly prohibited under the Act.
The standard defenses of network service providers would be that they exercised due care and the contravention did not occur with their knowledge or negligence.
Distinguish Between
Question.1: Distinguish between hacking and passing off.
Answer:
Difference between hacking and passing off
Question 2: Distinguish between ‘Computer network’ and ‘Computer system’.
Answer:
Difference between ‘Computer network’ and ‘Computer system’
Descriptive Questions
Question.1: Define the following terms
- Electronic record
- Digital signature
- Originator
- Asymmetric crypto system
- Network service providers
- Domain name
Answer:
‘Electronic record’ as per Section 2(1)(t) includes information recorded by way of data or images in electronic form and recorded in any media, viz, microfilm, microfiche etc.
Section 4 of the Information Technology Act, 2000 provides that information provided in electronic form, including but not limited to data, images, databases, texts etc., will be given the same importance and legal recognition as is given to written, printed or typewritten information.
‘Digital signature’ is defined in Section 2(1)(p). This definition provides for electronic means of validating of electronic records by the procedure prescribed under the Information Technology Act, 2000.
This is done with the help of a signature in electronic form, which is registered with the Certifying Authority under the Act.
‘Originator’ means a person who sends or initiates an electronic message. This excludes all intermediaries who just act as a link between the sender and recipient of messages. [Section 2(1)(za)]
This definition helps to judge the authenticity of messages, i.e. if a message has been sent by a known originator, then it can be deemed to be authentic.
‘Asymmetric cryptosystem’, according to the definition of Section 2(1)(f) of the Information Technology Act, 2000, means a key pair that provides safety and authenticity to the electronic records being transmitted.
The key pair consists of a public and a private key, both of which are needed to ‘sign’ an electronic document digitally.
‘Network service providers’ have been defined in Section 2(1)(w) of the Information Technology Act, 2000. These are intermediaries who do not initiate the creation or passing off a message but help in providing facilities for the same.
They can help in the receiving or sending of a message on behalf of another. Section 79 exempts them from liability they might incur for the actions of third parties making use of their services and doing something that is expressly prohibited under the Act.
The standard defenses of network service providers would be that they exercised due care and the contravention did not occur with their knowledge or negligence.
‘Domain name’ is a unique address pertaining to a website. This is where all communications using the net will be addressed. It helps to register the domain name as the address then becomes exclusive and identifies the company or person whose website it is. It also makes finding the company online easier.
Question.2: When is a digital signature deemed to be secure?
Answer:
A digital signature deemed to be secure
‘Digital signature’ is defined in Section 2(1)(p). This definition provides for electronic means of validating of electronic records by the procedure prescribed under the Information Technology Act, 2000.
This is done with the help of a signature in electronic form, which is registered with the Certifying Authority under the Act.
It is deemed to be secure when it is as per the requirements of Section 15 of the Information Technology Act, 2000. They are as under:
- If the signature is unique and controlled by the person affixing it.
- It distinguishes the subscriber, i.e. the person affixing or using it.
It is so linked with the electronic record to which it is attached that if the record were changed in any way, doing so would nullify the authenticity or veracity of the signature.
Question.3: Define hacking and explain its effects.
Answer:
Hacking
‘Hacking’ means causing or attempting to cause loss or damage to anyone by removing or changing any information stored in a computer system or allied resources. This is done by unauthorized access of the information.
The punishment for hacking is imprisonment upto three years, or fine upto rupees two lacs, or both. (Section 66 of the Information Technology Act, 2000). Hacking definitely affects the financial returns of a company, since the hacker takes a large slice of the profits.
It might also cause loss of reputation to the company whose Id is hacked, or it may even cause company secrets to be brought out into the open if the confidential information of the company is accessed.
Question.4: Explain the terms ‘computer contaminant’ and ‘computer virus’.
Answer:
The terms ‘computer contaminant’ and ‘computer virus’
The terms are contained in Section 43 of the Information Technology Act,2000. ‘Computer contaminant’ means a program or a series of commands given to a computer that alters, deletes or releases programs within the computer and in doing so alters the ordinary working of the system or network. (Explanation to the section)
‘Computer virus’ means a program, set of instructions or information set into a computer to affect its functioning in any way. It operates by affixing itself to the computer’s resources and replicating itself when a program is run.
Section 43 of the Act provides for penalty for damages inflicted on a computer or computer resource, without the owner’s permission or knowledge. The damages are to be paid by way of compensation upto an amount of rupees one crore.
Question.5: When can a digital signature be revoked?
Answer:
According to the Information Technology Act, 2000, Section 38, a digital signature can be revoked by the Certifying Authority under the following circumstances –
- When the person in whose name it has been registered requests, by himself or through an authorized representative, and gives it in writing that he wishes for it to be cancelled.
- When the subscriber expires.
- When he becomes insolvent.
- When the company or firm that is the subscriber is wound up or dissolved.
- When the Certifying Authority is of the opinion that the certificate has been obtained by misrepresentation of a material fact or by fraud.
- When some essential requirement for obtaining the certificate has not been fulfilled.
- When the private key of the certificate has been breached.
In all the cases where the revocation takes place by an action taken suo motu by the Certifying Authority, the subscriber will be given an opportunity
of being heard, and upon the revocation of the certificate, the subscriber will be intimated of the fact.
Practical Questions
Question.1 : Amrish was found guilty of damaging the data stored in a computer. The adjudicating officer fined him ₹ 1,00,000 and directed the amount to be paid to the aggrieved person. Advise Amrish about the course of action against this decision under the Information Technology Act, 2000.
Answer:
Amrish has the right to file an appeal to the Cyber Appellate Tribunal (CAT) against the order passed by the adjudicating officer. The limitation period for filing the appeal is forty-five days. If he is unsatisfied with the order passed by the CAT, he may prefer an appeal to the High Court within a period of sixty days.
However, since under Section 43 of the Act, damaging data stored in a computer is liable to be punished with a penalty not exceeding one crore rupees, the remedy will only work in his favor if it is proven that he is not guilty of the offence.
Question.2: Abhay downloaded secret data from the computer network of a foreign company engaged in the manufacture of aircrafts. He was prosecuted and fined One lakh by the adjudicating officer under section 43 of the Information Technology Act, 2000. Is any remedy available to Abhay?Advise.
Answer:
Abhay has the right to file an appeal to the Cyber Appellate Tribunal (CAT) against the order passed by the adjudicating officer. The limitation period for filing the appeal is forty-five days. If he is unsatisfied with the order passed by the CAT, he may prefer an appeal to the High Court within a period of sixty days.
However, since under Section 43 of the Act, downloading secret data stored in a computer is liable to be punished with a penalty not exceeding one crore rupees, the remedy will only work in his favor if it is proven that he is not guilty of the offence.
Question.3: Chanchal sues Indian Online Ltd. (IOL) for allowing a subscriber Rajat to use its chatroom for making video tapes and photographs of child pornography in which Chanchal’s minor son appears. The complaint alleged that IOL was negligent per se in allowing Rajat to use its facilities for producing obscene materials, therefore, is liable under criminal law and under the Information Technology Act, 2000. IOL contends that it has no knowledge of such transmission of unlawful information. Decide the liability of IOL.
Answer:
‘Network service providers’ have been defined in Section 2(1)(w) of the Information Technology Act, 2000. These are intermediaries who do not initiate the creation or passing off a message but help in providing facilities for the same.
They can help in the receiving or sending of a message on behalf of another. Section 79 exempts them from liability they might incur for the actions of third parties making use of their services and doing something that is expressly prohibited under the Act.
The standard defenses of network service providers would be that they exercised due care and the contravention did not occur with their knowledge or negligence.
Hence, IOL, being a network service provider, can prove that the offence did not occur because of their negligence. Hence, they would not be liable for the subscriber and hence not punishable.
